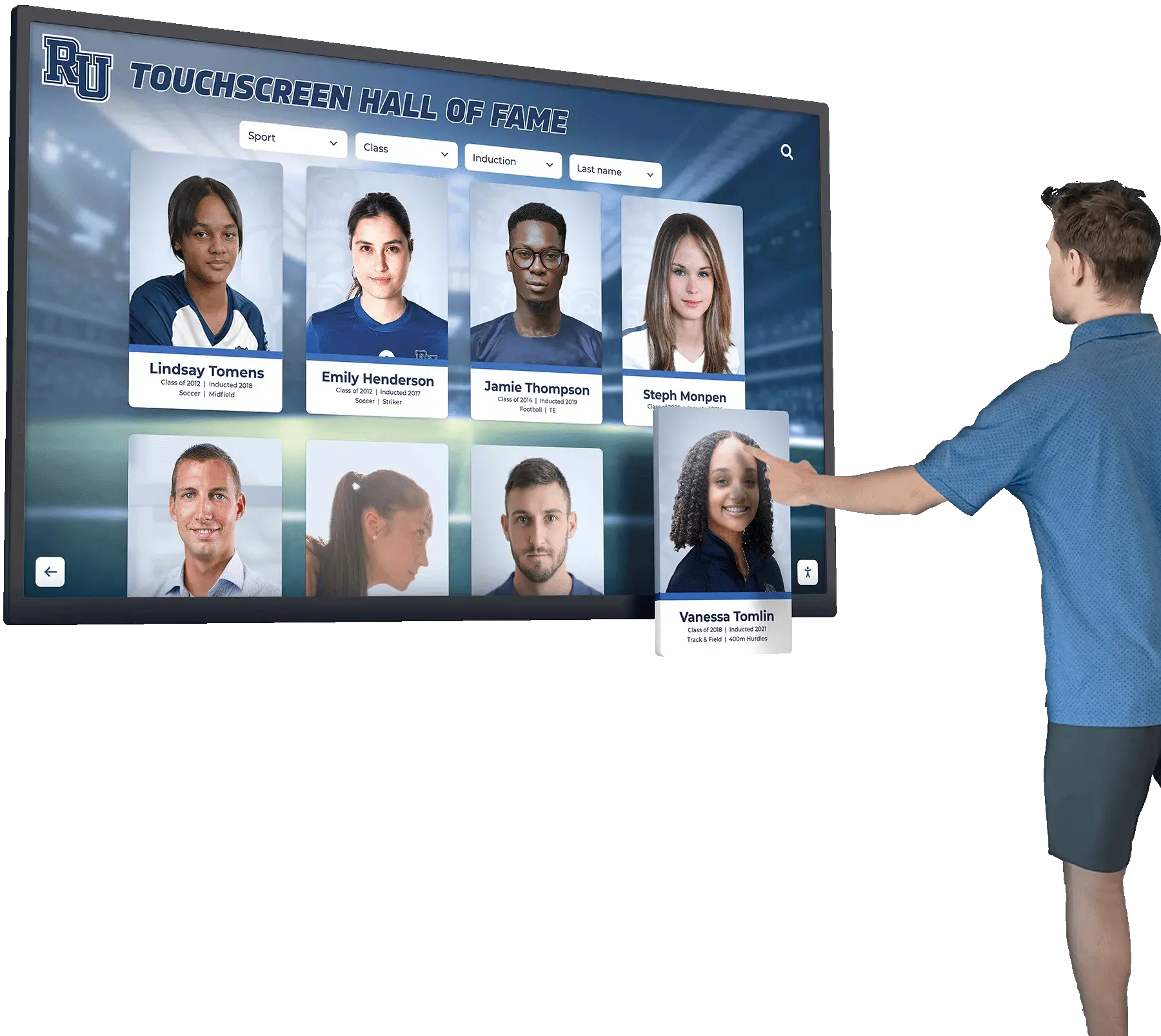
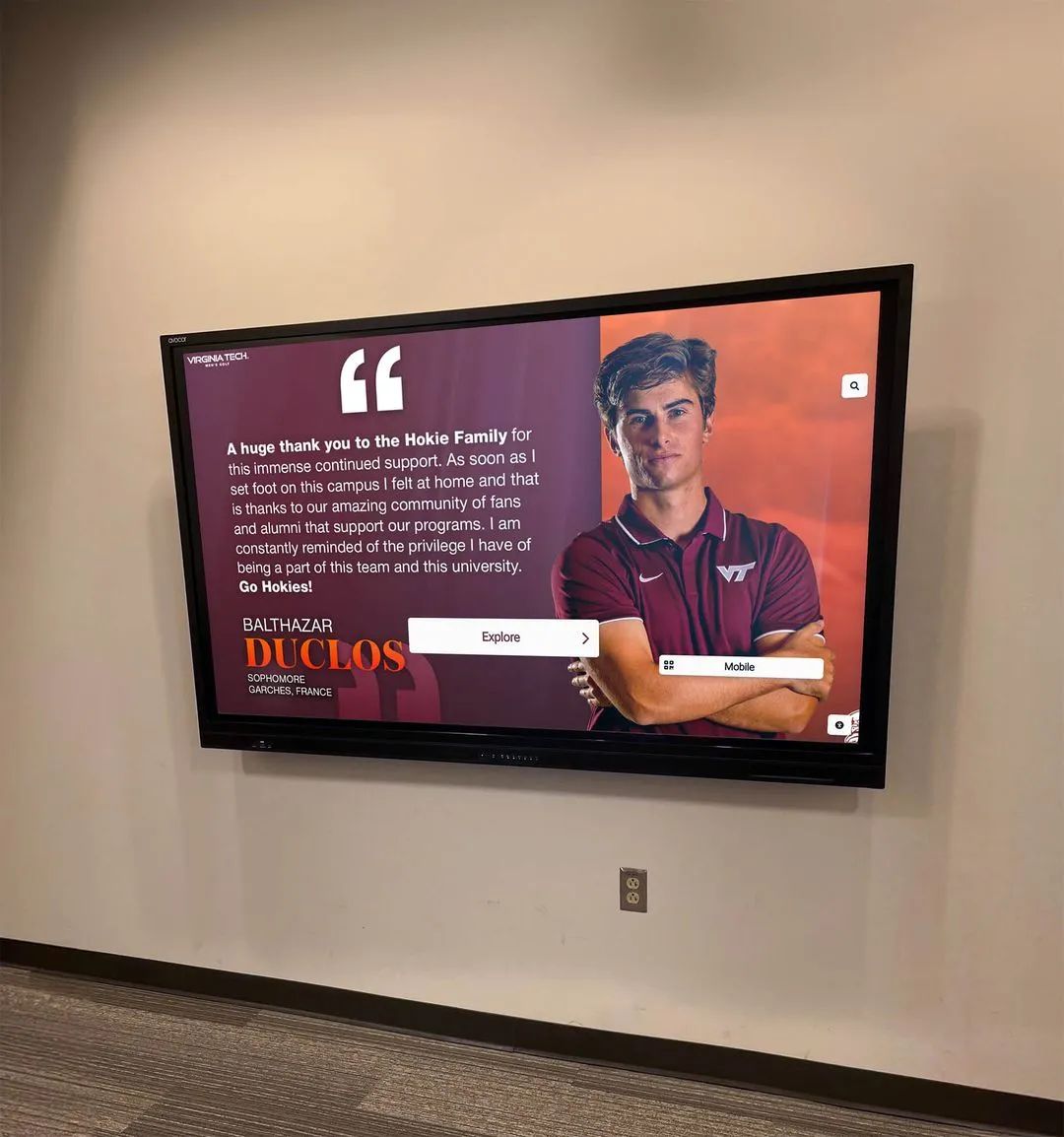
Introduction: Why Data Privacy Matters in Digital Recognition Systems
As schools and organizations increasingly adopt digital recognition systems to celebrate achievements and build community engagement, data privacy and security concerns have become paramount. With interactive displays handling sensitive information about students, employees, alumni, and community members, implementing robust privacy protections isn’t just best practice—it’s a legal necessity and ethical imperative.
Recent regulatory changes in 2026, including enhanced FERPA enforcement and new state-level privacy laws, require organizations to demonstrate comprehensive data protection strategies. Digital recognition platforms that fail to implement adequate safeguards face significant legal liability, financial penalties, and reputation damage that can undermine community trust and organizational mission.
Table of Contents
- Understanding Privacy Regulations and Legal Requirements
- FERPA Compliance for Educational Digital Recognition
- Employee Data Protection in Workplace Recognition Systems
- Essential Security Measures and Technical Safeguards
- Data Collection and Consent Management Best Practices
- Third-Party Vendor Risk Management and Due Diligence
- Incident Response Planning and Breach Management
- Privacy by Design Implementation Strategies
- Ongoing Compliance Monitoring and Auditing
- Future-Proofing Your Privacy Program
1. Understanding Privacy Regulations and Legal Requirements
Digital recognition systems operate within a complex regulatory environment where multiple privacy laws intersect, creating compliance obligations that vary by organization type, geographic location, and the populations served. Understanding this landscape is essential for implementing legally compliant recognition programs.
Federal Privacy Law Foundation
FERPA (Family Educational Rights and Privacy Act): Educational institutions receiving federal funding must comply with FERPA, which governs access to and disclosure of student education records. In 2026, enforcement has intensified with new guidance on “reasonable methods” for protecting student privacy, particularly regarding automated systems and facial recognition technology.
COPPA (Children’s Online Privacy Protection Act): Organizations serving children under 13 must comply with COPPA requirements for parental consent before collecting, using, or disclosing personal information. Digital recognition systems displaying information about elementary students require careful consent management and data minimization practices.
State-Level Privacy Regulations
California Consumer Privacy Act (CCPA) and California Privacy Rights Act (CPRA): Organizations serving California residents must provide transparency about data collection, use, and sharing practices while offering consumers rights to access, delete, and correct their personal information. Recognition systems must accommodate these rights through appropriate technical and administrative measures.
Texas Privacy Protection Act (2026): The Texas Privacy Protection Act became fully effective January 2026, requiring comprehensive disclosure of monitoring activities in workplace environments. Employers must provide detailed notice about data collection, storage, and sharing practices for employee recognition systems.
Illinois Biometric Information Privacy Act (BIPA): Organizations using facial recognition or other biometric technologies for recognition purposes must obtain explicit written consent and provide clear retention and destruction timelines. Violations carry significant financial penalties and legal liability.
Virginia Consumer Data Protection Act (VCDPA): Virginia residents have rights regarding personal data processing, including the right to access, correct, delete, and obtain copies of their data. Recognition systems must implement processes for handling these requests efficiently and accurately.
Multi-State Complexity Management: Organizations operating across multiple states face varying requirements ranging from strict notification mandates to comprehensive consent protocols. Compliance strategies must accommodate the most restrictive applicable laws while maintaining operational efficiency.
Industry-Specific Compliance Requirements
Healthcare Recognition Systems: Healthcare organizations implementing employee recognition displays must consider HIPAA requirements if any patient information could be inferred or accessed through recognition content. This includes careful consideration of staff recognition in patient care areas.
Financial Services Recognition Programs: Financial institutions face additional privacy obligations under the Gramm-Leach-Bliley Act and other financial privacy regulations when implementing employee or customer recognition systems that could interact with financial data systems.
International Privacy Considerations
GDPR Compliance for Global Organizations: Organizations with international operations or European visitors must consider GDPR requirements for data processing, including lawful basis determination, data subject rights accommodation, and international data transfer safeguards.
Cross-Border Data Transfer Management: Digital recognition systems using cloud-based platforms must ensure compliance with international data transfer requirements, including appropriate safeguards for data processed or stored outside the organization’s home country.
2. FERPA Compliance for Educational Digital Recognition
Educational institutions implementing digital recognition systems must navigate FERPA requirements while creating engaging celebration platforms that honor student achievements. Understanding FERPA’s application to modern recognition technology ensures compliance while maximizing educational and community benefits.
Education Records Definition and Scope
FERPA Coverage Determination: FERPA protects “education records” defined as records directly related to students and maintained by educational agencies or institutions. Digital recognition content about student achievements typically qualifies as education records requiring protection under FERPA’s disclosure and access provisions.
Directory Information Considerations: Schools may designate certain information as “directory information” that can be disclosed without consent, including name, address, telephone listing, email address, date and place of birth, major field of study, participation in activities and sports, weight and height of athletic team members, dates of attendance, degrees and awards received, and most recent educational agency attended.
Consent Management and Disclosure Controls
Parental Consent Requirements: For students under 18, schools must obtain written consent before disclosing education records, except in specific circumstances outlined in FERPA. Digital recognition systems must implement consent tracking and management capabilities to ensure appropriate authorization for all displayed content.
Student Rights Upon Reaching Age 18: When students reach age 18 or attend postsecondary institutions, FERPA rights transfer from parents to eligible students. Recognition systems must accommodate this transition through appropriate access controls and consent management processes.
Legitimate Educational Interest: School officials with legitimate educational interests may access education records without consent. Digital recognition systems should implement role-based access controls that align with institutional definitions of legitimate educational interest.
Annual Notification Requirements: FERPA requires annual notification of privacy rights to parents and eligible students. Digital recognition implementations should be included in these notifications with clear explanations of data collection, use, and sharing practices.
Opt-Out Procedures: Schools must provide reasonable procedures for parents and eligible students to opt out of directory information disclosures. Recognition systems must accommodate opt-out requests promptly and completely.
Record Keeping and Audit Trails: FERPA requires maintaining records of access to education records. Digital recognition systems should implement comprehensive logging capabilities that track who accessed what information and when.
Technology-Specific FERPA Considerations
Facial Recognition and Biometric Data: The Department of Education has indicated that unreviewed school surveillance footage is generally not “directly related” to a student until a student has been associated with the footage. However, facial recognition software may change this dynamic, requiring careful consideration of FERPA implications.
Automated Content Generation: AI-powered systems that automatically generate recognition content using student data must ensure all generated content complies with FERPA disclosure requirements and maintains accuracy standards required for education records.
Vendor Relationship Management
Service Provider Agreements: Organizations providing digital recognition services to schools become “school officials” under FERPA when performing institutional services or functions. Service agreements must include appropriate FERPA compliance provisions and data protection requirements.
Data Sharing and Third-Party Integration: Integration with other educational technology systems must comply with FERPA requirements for data sharing between service providers and ensure appropriate safeguards for education records throughout the technology ecosystem.
3. Employee Data Protection in Workplace Recognition Systems
Workplace digital recognition systems handle diverse employee data requiring comprehensive protection strategies that balance celebration goals with privacy rights and legal compliance obligations. Organizations must implement robust data governance frameworks that protect employee information while enabling meaningful recognition programs.
Employee Privacy Rights and Expectations
Reasonable Expectation of Privacy: Employees maintain reasonable expectations of privacy in certain workplace contexts, even while participating in recognition programs. Organizations must balance recognition goals with employee privacy rights through transparent policies and appropriate consent mechanisms.
Biometric Data and Facial Recognition: Employee recognition systems using biometric identifiers face strict regulatory requirements. California Civil Code Section 1798.140 requires explicit written consent before collecting biometric identifiers and mandates clear retention and destruction timelines.
Consent and Participation Management
Voluntary Participation Principles: Employee participation in recognition programs should be voluntary, with clear opt-in and opt-out mechanisms. Organizations should not penalize employees who choose limited participation in recognition display systems or social sharing features.
Granular Consent Controls: Recognition systems should enable granular consent management allowing employees to control different aspects of their recognition participation, including photo use, biographical information sharing, and external social media integration.
Ongoing Consent Management: Employee consent preferences may change over time, requiring recognition systems to accommodate updates, modifications, and withdrawal of consent with appropriate technical and administrative processes.
Sensitive Information Categories: Special protection is required for sensitive employee information including health data, financial information, and personal circumstances that may be relevant to certain types of recognition programs.
Cross-Jurisdictional Considerations: Multi-location organizations must accommodate varying privacy requirements across different jurisdictions, implementing systems that meet the most restrictive applicable standards.
Union and Collective Bargaining Agreements: Unionized workplaces may have specific privacy provisions in collective bargaining agreements that affect employee recognition program design and implementation.
Data Minimization and Purpose Limitation
Collection Necessity Assessment: Organizations should implement data minimization practices ensuring only necessary information is collected for recognition purposes. Regular assessment of data collection practices prevents excessive accumulation of employee information.
Purpose Specification and Limitation: Employee data collected for recognition purposes should be used only for those specified purposes unless additional consent is obtained. Clear purpose statements help maintain trust and ensure legal compliance.
International Employee Privacy Compliance
GDPR Compliance for European Employees: Organizations with European employees must comply with GDPR requirements including lawful basis determination for data processing, data subject rights accommodation, and appropriate safeguards for international data transfers.
Multi-National Privacy Framework: Global organizations need comprehensive privacy frameworks that accommodate varying international privacy requirements while maintaining operational efficiency and consistent recognition program implementation.
4. Essential Security Measures and Technical Safeguards
Implementing robust technical security measures forms the foundation of effective privacy protection for digital recognition systems. Organizations must deploy multiple layers of security controls that protect data throughout its lifecycle while maintaining system usability and performance.
Encryption and Data Protection
Data Encryption Standards: All personal data in digital recognition systems should be encrypted using current industry standards. Data must be encrypted both at rest (when stored in databases or on devices) and in transit (during transmission between systems or locations) to prevent unauthorized access during breaches or interception attempts.
End-to-End Encryption Implementation: Recognition platforms should implement end-to-end encryption ensuring that data remains protected from collection through display, with encryption keys managed securely and rotated regularly to maintain optimal security posture.
Database Security and Access Controls: Database systems storing recognition content require comprehensive security measures including encrypted storage, access logging, regular security updates, and network segregation to prevent unauthorized access and maintain data integrity.
Access Management and Authentication
Multi-Factor Authentication (MFA): All administrative access to digital recognition systems should require multi-factor authentication combining something users know (password), have (token or phone), and/or are (biometric identifier) to prevent unauthorized access even with compromised credentials.
Role-Based Access Control (RBAC): Recognition systems should implement granular role-based access controls ensuring users can only access information necessary for their legitimate responsibilities. Regular access reviews ensure permissions remain appropriate as roles change.
Principle of Least Privilege: Administrative and user accounts should receive only the minimum access necessary to perform required functions, with elevated privileges granted temporarily and logged appropriately.
Session Management and Timeout: Recognition systems should implement appropriate session management including automatic logout after periods of inactivity and secure session handling to prevent unauthorized access through unattended devices.
Audit Logging and Monitoring: Comprehensive logging of system access, data modifications, and administrative actions enables security monitoring and provides evidence for compliance audits and incident investigation.
Network Security and Infrastructure Protection
Secure Network Architecture: Digital recognition systems should operate within secure network environments with appropriate firewalls, intrusion detection systems, and network segmentation to prevent unauthorized access and lateral movement in case of breaches.
Cloud Security Considerations: Cloud-based recognition platforms require careful evaluation of cloud service provider security measures, including data residency controls, shared responsibility model understanding, and appropriate contractual safeguards for data protection.
Regular Security Assessment and Updates
Vulnerability Management: Recognition systems require regular security assessments including vulnerability scanning, penetration testing, and security code reviews to identify and remediate potential security weaknesses before they can be exploited.
Software Updates and Patch Management: Maintaining current software versions with timely security updates prevents exploitation of known vulnerabilities. Automated patch management systems can help ensure consistent update application across all system components.
5. Data Collection and Consent Management Best Practices
Effective consent management ensures that digital recognition systems collect and use personal data with appropriate authorization while providing transparency about data practices. Organizations must implement sophisticated consent management capabilities that accommodate diverse privacy preferences and regulatory requirements.
Consent Framework Design and Implementation
Informed Consent Principles: Consent for recognition program participation must be informed, specific, freely given, and withdrawable. Organizations should provide clear explanations of data collection purposes, retention periods, sharing practices, and individual rights before obtaining consent.
Granular Consent Controls: Recognition systems should enable individuals to provide granular consent for different aspects of participation including photo use, biographical information sharing, social media integration, and external communications about their achievements.
Consent Documentation and Tracking: Organizations must maintain comprehensive records of consent including when it was obtained, what was authorized, any modifications or withdrawals, and evidence of the consent process for compliance documentation and audit purposes.
Age-Appropriate Consent Management
Parental Consent for Minors: Recognition programs serving minors must obtain appropriate parental consent before collecting, using, or displaying personal information. Systems should accommodate parental rights to access, modify, and withdraw consent for their children’s participation.
Age Verification and Transition: Recognition systems must accommodate the transition of privacy rights when minors reach the age of majority, ensuring appropriate consent transfer and continued compliance with applicable privacy regulations.
COPPA Compliance for Young Children: Programs serving children under 13 must comply with enhanced COPPA requirements including parental notification, consent verification, and limited data collection practices.
Ongoing Consent Management: Consent preferences may change over time, requiring recognition systems to accommodate updates, modifications, and complete withdrawal of consent with appropriate technical and administrative processes.
Cross-Generational Family Considerations: Recognition programs often involve families across multiple generations, requiring careful consideration of different privacy preferences and consent requirements for various family members.
Data Collection Minimization Strategies
Purpose Specification and Limitation: Organizations should clearly define and document the specific purposes for data collection in recognition programs, collecting only information necessary to achieve those stated purposes and avoiding excessive data accumulation.
Data Quality and Accuracy: Recognition systems should implement processes ensuring data accuracy and currency, including regular verification procedures and mechanisms for individuals to review and correct their information.
Consent Withdrawal and Right to be Forgotten
Withdrawal Process Design: Organizations must provide simple, accessible mechanisms for consent withdrawal that are as easy to use as the original consent process, with clear timelines for processing withdrawal requests and removing associated data.
Data Deletion and System Cleanup: Consent withdrawal should trigger comprehensive data removal including recognition content, archived materials, backup systems, and any derivative works created using the individual’s information.
Solutions like Rocket Alumni Solutions incorporate sophisticated consent management capabilities that enable organizations to implement compliant recognition programs while respecting individual privacy preferences and accommodating diverse regulatory requirements across different jurisdictions.
6. Third-Party Vendor Risk Management and Due Diligence
Digital recognition systems often rely on various third-party vendors for cloud hosting, data processing, analytics, and integration services. Managing these vendor relationships requires comprehensive risk assessment, contractual safeguards, and ongoing monitoring to ensure data protection throughout the vendor ecosystem.
Vendor Selection and Due Diligence
Security Assessment and Certification: Organizations should evaluate vendor security practices through comprehensive assessments including SOC 2 Type II reports, ISO 27001 certifications, and detailed security questionnaires covering data protection, access controls, incident response, and business continuity planning.
Privacy Program Evaluation: Vendor privacy programs should align with organizational requirements and applicable regulations. Evaluation should include privacy policy analysis, data handling practices assessment, international data transfer safeguards, and compliance with relevant privacy regulations.
Financial Stability and Business Continuity: Recognition systems often store valuable historical data requiring long-term vendor stability. Financial assessment and business continuity planning help ensure continued service availability and data protection even during vendor transitions.
Contract Terms and Data Protection Agreements
Data Processing Agreements (DPAs): Comprehensive data processing agreements should specify the purposes and legal basis for data processing, vendor obligations for data protection, limitations on data use and sharing, and individual rights accommodation procedures.
Security Requirements and Standards: Vendor contracts should specify minimum security requirements including encryption standards, access controls, logging and monitoring requirements, and incident notification procedures.
Compliance and Audit Rights: Organizations should retain rights to audit vendor compliance with contractual obligations and applicable regulations, either through direct audits or review of independent certification reports.
Data Return and Destruction: Contracts should specify procedures for data return or secure destruction upon contract termination, including timelines, verification procedures, and certification of complete data removal.
Liability and Indemnification: Appropriate liability allocation and indemnification provisions help protect organizations from vendor-caused privacy breaches or compliance failures.
Ongoing Vendor Management and Monitoring
Regular Risk Assessment: Vendor risk profiles change over time requiring periodic reassessment of security practices, financial stability, compliance status, and overall risk posture to ensure continued suitability for recognition system data processing.
Performance Monitoring and Metrics: Organizations should establish key performance indicators for vendor data protection including security incident frequency, response times for data subject requests, system availability, and compliance audit results.
Vendor Incident Response and Communication
Incident Notification Requirements: Vendor contracts should specify rapid notification procedures for security incidents or privacy breaches affecting recognition system data, with clear timelines and required information for incident assessment and response.
Communication and Coordination: Effective vendor incident response requires coordinated communication between organization and vendor incident response teams, including roles and responsibilities, escalation procedures, and stakeholder notification requirements.
7. Incident Response Planning and Breach Management
Comprehensive incident response planning enables organizations to respond effectively to privacy breaches or security incidents affecting digital recognition systems. Well-designed response procedures minimize harm to affected individuals while ensuring compliance with legal notification requirements and maintaining community trust.
Incident Response Framework Development
Incident Classification and Assessment: Organizations should establish clear criteria for classifying privacy incidents by severity, scope, and potential harm to affected individuals. Classification systems should align with regulatory notification requirements and internal escalation procedures.
Response Team Structure and Roles: Incident response teams should include representatives from IT security, legal, communications, human resources, and senior management with clearly defined roles, responsibilities, and decision-making authority for different types of incidents.
Communication Protocols and Procedures: Response procedures should specify internal and external communication requirements including timelines, responsible parties, and content requirements for notifications to affected individuals, regulators, and other stakeholders.
Breach Detection and Initial Response
Monitoring and Detection Systems: Recognition systems should implement comprehensive monitoring capabilities that can detect unauthorized access, unusual data activity, system modifications, and other indicators of potential security incidents or privacy breaches.
Initial Assessment and Containment: Upon incident detection, response teams should quickly assess the scope and severity of the incident while implementing containment measures to prevent further unauthorized access or data compromise.
Evidence Preservation: Incident response procedures should ensure proper preservation of digital evidence for investigation and potential legal proceedings while maintaining system integrity and business continuity.
Impact Assessment and Risk Evaluation: Comprehensive impact assessment should evaluate the types and amount of data affected, potential harm to individuals, and likelihood of misuse to inform notification decisions and remediation strategies.
Regulatory Notification Requirements: Response procedures must accommodate various regulatory notification timelines including FERPA requirements, state breach notification laws, and other applicable privacy regulations.
Stakeholder Communication and Notification
Individual Notification Procedures: Organizations must provide timely, clear notification to affected individuals explaining what happened, what information was involved, what steps are being taken to address the incident, and what individuals can do to protect themselves.
Regulatory and Law Enforcement Coordination: Incident response should include appropriate notification and coordination with regulatory agencies, law enforcement, and other authorities as required by applicable laws and organizational policies.
Post-Incident Recovery and Improvement
Remediation and System Recovery: Response procedures should specify steps for system recovery, security enhancement, and prevention of similar incidents including technical improvements, policy updates, and training enhancements.
Lessons Learned and Process Improvement: Post-incident reviews should identify lessons learned and opportunities for improvement in detection capabilities, response procedures, communication effectiveness, and prevention strategies.
Solutions like Rocket Alumni Solutions provide comprehensive incident response support including rapid technical assistance, communication templates, and coordination with organizational response teams to ensure effective incident management while maintaining recognition program continuity.
8. Privacy by Design Implementation Strategies
Privacy by Design principles ensure that data protection considerations are embedded throughout digital recognition system design, development, and operation rather than added as an afterthought. Implementing these principles creates more effective privacy protection while often improving system usability and efficiency.
Proactive Privacy Integration
Early Privacy Assessment: Privacy considerations should be integrated from the earliest stages of recognition system planning including needs assessment, vendor selection, system design, and implementation planning to ensure comprehensive protection throughout the system lifecycle.
Default Privacy Settings: Recognition systems should be designed with privacy-protective settings as defaults, requiring explicit user action to enable broader data sharing or reduced privacy protection rather than requiring users to discover and activate privacy features.
User-Centric Design Principles: Privacy controls should be designed for usability with clear language, intuitive interfaces, and logical organization that enables users to understand and control their privacy settings without technical expertise or extensive training.
Technical Privacy Implementation
Data Minimization by Design: System architecture should implement technical controls that limit data collection to necessary purposes, automatically delete data when no longer needed, and prevent access to unnecessary information even by system administrators.
Purpose Limitation Controls: Technical controls should prevent data collected for one purpose from being automatically used for other purposes without appropriate consent or legal authorization, maintaining clear separation between different data processing activities.
Transparency and Visibility: Systems should provide clear visibility into data processing activities including what data is collected, how it’s used, who has access, and when it will be deleted or anonymized.
Security by Design: Privacy protection requires robust security measures implemented at the architectural level including encryption, access controls, audit logging, and intrusion detection capabilities.
Cross-Border Compliance: System design should accommodate international privacy requirements including data residency controls, transfer mechanism safeguards, and compliance with multiple regulatory frameworks.
Organizational Privacy Integration
Privacy Impact Assessment (PIA): Comprehensive privacy impact assessments should evaluate potential privacy risks, identify mitigation strategies, and document privacy design decisions for recognition system implementations.
Training and Awareness Programs: Staff involved in recognition system operation should receive privacy training covering legal requirements, technical controls, incident response procedures, and best practices for data protection.
Continuous Privacy Improvement
Regular Privacy Review: Recognition system privacy practices should be reviewed regularly to ensure continued effectiveness, identify improvement opportunities, and accommodate changing legal requirements or organizational needs.
User Feedback Integration: Privacy program improvement should incorporate user feedback about privacy concerns, control preferences, and suggestions for enhanced privacy protection to ensure privacy measures meet community needs and expectations.
9. Ongoing Compliance Monitoring and Auditing
Effective compliance monitoring ensures that digital recognition systems maintain privacy and security standards over time through systematic assessment, measurement, and improvement. Regular auditing helps identify compliance gaps before they become violations while demonstrating due diligence to regulators and stakeholders.
Compliance Monitoring Framework
Key Performance Indicators (KPIs): Organizations should establish measurable indicators of privacy program effectiveness including incident frequency, response times for data subject requests, training completion rates, vendor compliance scores, and audit finding resolution times.
Automated Monitoring Systems: Recognition platforms should implement automated monitoring capabilities that can detect policy violations, unusual access patterns, data quality issues, and other indicators requiring attention or investigation.
Regular Compliance Assessment: Systematic compliance assessments should evaluate adherence to applicable privacy laws, organizational policies, contractual obligations, and industry best practices through structured review processes.
Internal Audit Procedures
Audit Planning and Scheduling: Organizations should establish regular audit schedules with appropriate frequency based on risk assessment, regulatory requirements, and system complexity, ensuring comprehensive coverage of all privacy and security controls.
Documentation and Evidence Collection: Audit procedures should specify required documentation, evidence collection methods, and record retention requirements to support compliance demonstration and regulatory examination.
Finding Classification and Prioritization: Audit findings should be classified by risk level and compliance impact with appropriate prioritization for remediation efforts and resource allocation.
Remediation Tracking and Verification: Systematic tracking of remediation efforts ensures timely resolution of compliance gaps with verification procedures confirming effective implementation of corrective measures.
Management Reporting and Oversight: Regular compliance reporting to senior management should provide visibility into privacy program effectiveness, emerging risks, and resource needs for continued compliance.
External Audit and Certification
Independent Security Assessment: Organizations should engage qualified independent assessors to evaluate recognition system security controls, privacy practices, and compliance with applicable standards and regulations.
Certification and Standards Alignment: Pursuing relevant certifications such as SOC 2 Type II, ISO 27001, or Privacy Shield successor frameworks provides external validation of privacy and security program effectiveness.
Regulatory Examination Preparation
Examination Readiness: Organizations should maintain examination-ready documentation including privacy policies, training records, incident response logs, audit reports, and vendor due diligence materials to facilitate regulatory reviews.
Regulatory Relationship Management: Proactive engagement with relevant regulatory agencies through industry associations, comment periods on proposed regulations, and professional development helps maintain awareness of evolving compliance requirements.
Solutions like Rocket Alumni Solutions provide comprehensive compliance monitoring tools including automated policy compliance checking, audit trail maintenance, and regulatory update notification to help organizations maintain ongoing compliance with evolving privacy requirements.
10. Future-Proofing Your Privacy Program
Digital privacy regulations continue evolving rapidly, requiring organizations to build adaptable privacy programs that can accommodate new requirements while maintaining effective protection and operational efficiency. Future-proofing strategies ensure recognition systems remain compliant as the regulatory landscape develops.
Emerging Privacy Trends and Regulations
Artificial Intelligence and Automated Decision-Making: New regulations increasingly address AI systems and automated decision-making processes. Recognition systems using AI for content generation, recommendation systems, or user personalization must prepare for enhanced transparency requirements and algorithmic accountability measures.
Biometric Data Protection Enhancement: Regulatory attention to biometric data continues expanding with new laws requiring enhanced consent procedures, data minimization practices, and security measures for facial recognition and other biometric technologies used in recognition systems.
Children’s Privacy Protection Evolution: Children’s privacy laws continue expanding in scope and requirements, with new age verification technologies, enhanced parental control requirements, and stricter limitations on data collection and use affecting recognition programs serving young people.
Adaptive Privacy Architecture
Flexible Consent Management: Future-ready recognition systems need sophisticated consent management capabilities that can accommodate varying regulatory requirements, cultural preferences, and individual privacy needs across different jurisdictions and communities.
Modular Privacy Controls: System architecture should enable rapid deployment of new privacy controls, consent mechanisms, and data handling procedures without requiring complete system redesign or extended service disruptions.
Cross-Border Data Governance: International privacy frameworks are becoming more complex, requiring recognition systems to accommodate varying data residency requirements, transfer mechanisms, and local privacy law compliance.
Interoperability and Standards: Emerging privacy standards and interoperability frameworks will require recognition systems to integrate with various privacy management platforms, consent management systems, and data portability tools.
Regulatory Technology Integration: RegTech solutions for privacy compliance monitoring, automated reporting, and regulatory change management will become increasingly important for maintaining compliance across multiple jurisdictions.
Technology Evolution and Privacy Impact
Quantum Computing and Encryption: Quantum computing developments may require enhanced encryption methods and key management practices to maintain data protection effectiveness against future cryptographic threats.
Internet of Things (IoT) Integration: Recognition systems may integrate with various IoT devices and sensors, requiring comprehensive privacy consideration for distributed data collection and processing across multiple connected devices.
Organizational Capabilities and Skills Development
Privacy Expertise Development: Organizations need internal privacy expertise including legal knowledge, technical skills, and program management capabilities to navigate evolving privacy requirements effectively.
Stakeholder Engagement and Communication: Future privacy programs must effectively engage with diverse stakeholders including community members, regulators, advocacy groups, and technology partners to maintain social license and compliance effectiveness.
Strategic Privacy Planning
Privacy Program Maturity Development: Organizations should assess and develop their privacy program maturity including governance structures, risk management capabilities, incident response effectiveness, and strategic privacy integration.
Investment and Resource Planning: Future privacy compliance will require ongoing investment in technology, training, and expertise development requiring strategic planning and resource allocation for sustained compliance capability.
Implementing comprehensive privacy and security measures for digital recognition systems protects individual rights while enabling organizations to celebrate achievements and build community engagement effectively. Solutions like Rocket Alumni Solutions incorporate leading-edge privacy and security capabilities designed to meet current requirements while providing flexibility for future regulatory developments.
Frequently Asked Questions About Digital Recognition Data Privacy
What are the most critical privacy risks with digital recognition systems?
How do FERPA requirements apply to digital recognition displays in schools?
What security measures are essential for digital recognition systems?
How should organizations manage consent for recognition program participation?
What should organizations look for in digital recognition system vendors regarding privacy and security?
How can organizations prepare for evolving privacy regulations affecting recognition systems?
Conclusion: Building Trust Through Comprehensive Privacy Protection
Implementing robust data privacy and security measures for digital recognition systems isn’t just about regulatory compliance—it’s about building and maintaining the trust essential for successful community engagement programs. Organizations that prioritize privacy protection create recognition platforms that community members feel confident participating in while avoiding the legal, financial, and reputational risks associated with privacy violations.
The evolving privacy landscape requires proactive approaches that go beyond minimum compliance to embrace privacy as a fundamental design principle and competitive advantage. Organizations implementing comprehensive privacy programs report higher community engagement, improved stakeholder trust, and stronger recognition program outcomes compared to those treating privacy as an afterthought.
Success requires understanding the complex regulatory environment, implementing appropriate technical and administrative safeguards, establishing effective governance and oversight processes, and maintaining adaptability for future requirements. Privacy-by-design principles ensure protection measures enhance rather than hinder recognition program effectiveness while providing sustainable compliance frameworks.
Digital recognition systems offer unprecedented opportunities to celebrate achievements and build community connections while respecting individual privacy rights and maintaining regulatory compliance. The investment in comprehensive privacy protection pays dividends through reduced legal risk, enhanced community trust, improved stakeholder engagement, and competitive differentiation in an increasingly privacy-conscious environment.
Solutions like Rocket Alumni Solutions are designed with privacy and security as foundational elements, providing comprehensive compliance capabilities, robust technical safeguards, and flexible adaptation to evolving requirements. Their privacy-first approach enables organizations to implement engaging recognition programs while maintaining the highest standards of data protection and regulatory compliance.
Ready to implement a privacy-compliant digital recognition system that builds community trust while celebrating achievements? Contact the Rocket Alumni Solutions team to discover how their comprehensive privacy and security framework can support your recognition program goals while exceeding regulatory requirements and community expectations.
Don’t let privacy concerns limit your community engagement potential. Join organizations nationwide who have discovered that robust privacy protection enhances rather than restricts effective recognition programs through solutions designed for both celebration and protection.