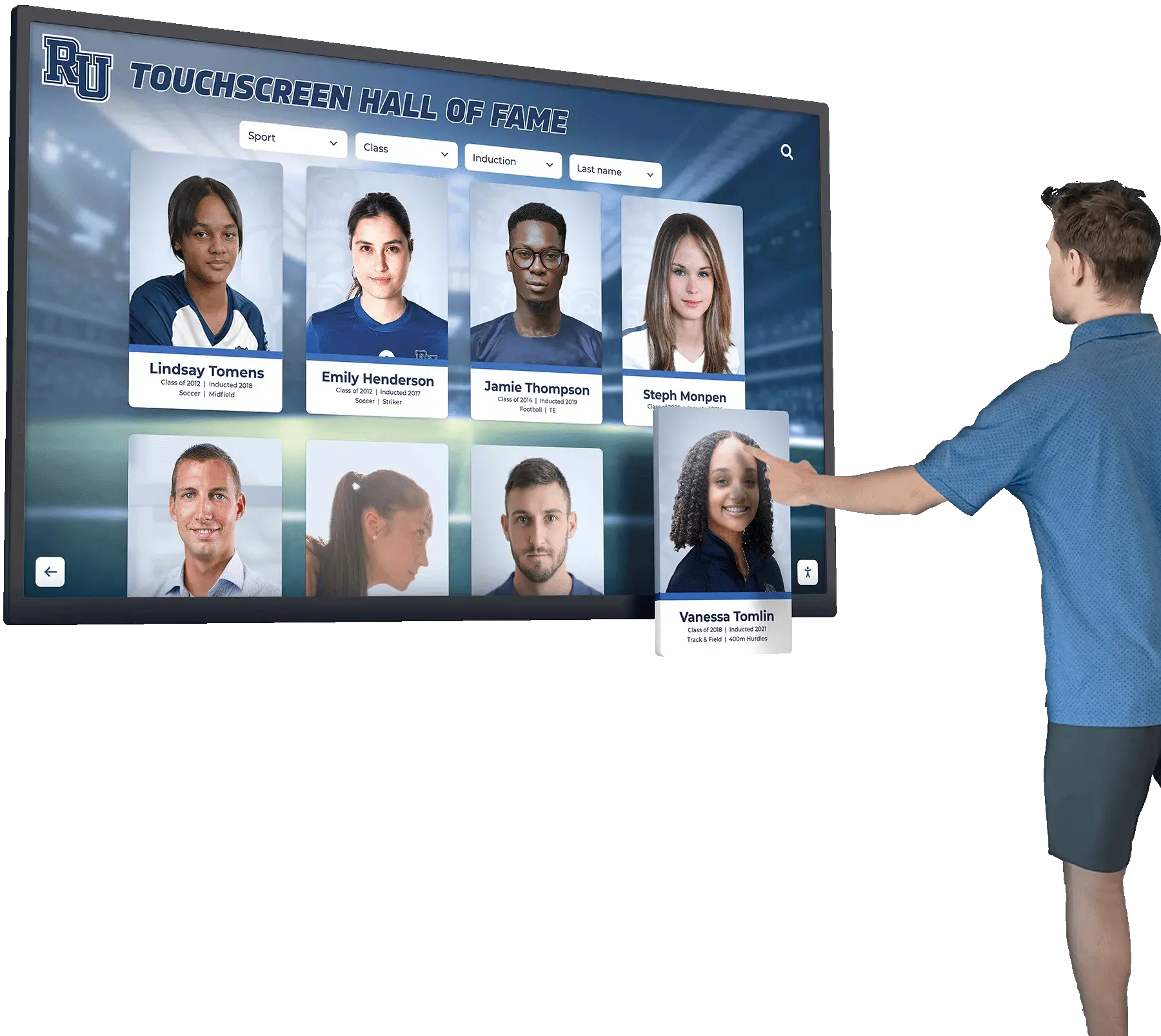
Cybersecurity teams operate under unique pressures. They defend organizational assets against persistent, sophisticated adversaries. They maintain vigilance across complex technology landscapes. They respond to incidents at all hours. They continuously update skills as attack methods evolve. In this demanding environment, trainees and early-career professionals particularly need acknowledgment that their efforts matter, their growth is visible, and their contributions are valued.
This comprehensive guide explores how organizations can implement cybersecurity trainee recognition programs that genuinely support professional development, strengthen retention, and cultivate the security culture necessary for organizational resilience. We’ll examine content strategies, implementation approaches, measurement frameworks, and industry applications that transform how organizations develop and retain cybersecurity talent.
Understanding the Cybersecurity Workforce Challenge
Before exploring recognition solutions, it’s essential to understand the workforce landscape shaping cybersecurity hiring and retention.
The Talent Gap and Retention Crisis
According to workforce data, the cybersecurity profession continues experiencing significant skill shortages. Organizations report difficulties filling open positions, with many security roles remaining vacant for months. This scarcity creates intense competition for qualified professionals and particularly affects efforts to develop entry-level and trainee pipeline programs.
Retention presents equally significant challenges. Early-career cybersecurity professionals frequently change employers, seeking better compensation, professional development opportunities, organizational culture, or work-life balance. The cost of losing trained security personnel extends beyond recruitment expenses—it includes knowledge loss, disrupted team dynamics, delayed projects, and increased risk exposure during transition periods.
Why Trainees Need Recognition
Cybersecurity trainees occupy particularly vulnerable positions regarding retention. They typically:
- Work through steep learning curves requiring intensive effort
- Make mistakes inherent to the learning process, sometimes with visible consequences
- Compare themselves to experienced professionals with years of expertise
- Question whether they can succeed in technically demanding roles
- Feel overwhelmed by the breadth of knowledge required
- Struggle with imposter syndrome common in technical fields
- Receive limited feedback beyond identification of errors or gaps
Without meaningful recognition acknowledging their progress, contributions, and potential, trainees may conclude they’re failing or that cybersecurity isn’t the right career path—even when they’re developing appropriately and showing strong promise.

Recognition programs specifically designed for security trainees address these challenges by making progress visible, celebrating appropriate development milestones, acknowledging contributions even while learning, and demonstrating organizational investment in their success.
The ROI of Security Trainee Recognition
Investment in trainee recognition delivers measurable returns through:
Improved Retention: When trainees feel valued and see clear development paths, they commit longer to their employers. Retaining a security trainee through their first three years of employment saves tens of thousands of dollars in replacement costs while building institutional knowledge.
Accelerated Competency Development: Recognition tied to skill milestones motivates trainees to pursue certifications, complete training modules, and seek challenging projects that develop capabilities faster than passive learning approaches.
Stronger Team Cohesion: Recognition programs that celebrate both individual and team achievements build collaborative cultures where experienced professionals mentor trainees and trainees support each other’s development.
Enhanced Employer Brand: Organizations known for developing cybersecurity talent attract better candidates. Recognition programs provide tangible evidence of commitment to professional development, differentiating employers in competitive markets.
Reduced Security Risk: Stable, well-trained teams familiar with organizational systems and threats provide stronger security than constantly rotating personnel requiring continuous onboarding.
Designing Effective Cybersecurity Trainee Recognition Programs
Recognition programs succeed when designed intentionally around trainee development paths and organizational security objectives.
Recognition Categories for Security Trainees
Rather than generic employee recognition, cybersecurity programs should acknowledge achievements specific to security professional development:
Technical Skill Milestones:
- Completing foundational certifications (Security+, CEH, CISSP)
- Mastering specific technical domains (network security, application security, cloud security)
- Successfully completing complex training scenarios or labs
- Demonstrating proficiency with security tools and platforms
- Contributing to security automation or tool development
- Publishing technical documentation or knowledge base articles
Incident Response Contributions:
- Participating in first incident response activities
- Identifying security indicators leading to threat detection
- Properly escalating security concerns through appropriate channels
- Contributing to post-incident analysis and lessons learned
- Maintaining composure during high-pressure security events
- Following established response procedures accurately
Continuous Learning Achievements:
- Completing professional development courses or workshops
- Earning industry certifications and specialized credentials
- Attending security conferences and presenting learnings to teams
- Contributing to security research or vulnerability analysis
- Participating in capture-the-flag competitions or security exercises
- Maintaining current knowledge of emerging threats and techniques
Collaboration and Mentorship:
- Effectively working across teams during security projects
- Mentoring newer trainees as they gain experience
- Contributing to team knowledge through documentation or presentations
- Participating actively in security team meetings and planning
- Helping improve security processes and procedures
- Building positive relationships with stakeholders outside security teams
Values Alignment:
- Demonstrating ethical behavior and professional integrity
- Maintaining confidentiality and handling sensitive information appropriately
- Showing resilience when facing complex challenges
- Exhibiting curiosity and proactive problem-solving approaches
- Contributing to positive team culture and colleague support
- Representing security teams professionally to broader organizations

Content Elements for Trainee Profiles
Comprehensive recognition profiles for cybersecurity trainees should include:
Professional Development Path:
- Educational background and relevant coursework
- Certifications earned and those in progress
- Training programs completed
- Technical specializations and areas of focus
- Career goals and development objectives
- Timeline showing progression since joining the organization
Technical Contributions:
- Projects participated in with role descriptions
- Security issues identified or resolved
- Tools or automation developed
- Documentation or knowledge base contributions
- Presentations delivered to teams or leadership
- Specific technical accomplishments with appropriate detail
Recognition and Awards:
- Formal recognition received from management
- Team member acknowledgments and peer testimonials
- Performance milestone achievements
- Competition results or external recognition
- Special project assignments based on demonstrated capability
- Progression through structured trainee program levels
Personal Elements:
- Professional photograph
- What attracted them to cybersecurity careers
- Memorable learning experiences or breakthrough moments
- Advice for others entering the field
- Interests and specializations within security
- Professional affiliations and community involvement
Multimedia Content:
- Video interviews discussing career journey and experiences
- Presentations on technical topics they’ve mastered
- Photos from security conferences, training events, or team activities
- Recorded demonstrations of technical skills or tool usage
- Testimonials from mentors, colleagues, or managers
Solutions like Rocket Alumni Solutions provide platforms designed for creating these comprehensive recognition profiles with intuitive content management systems that security teams can update as trainees progress through development milestones.
Implementation Strategies for Security Organizations
Successfully implementing trainee recognition requires careful planning addressing organizational structure, security culture, and practical constraints.
Integration with Security Training Programs
Recognition works most effectively when integrated directly into structured training programs rather than existing as separate initiatives:
Milestone-Based Recognition: Define clear development milestones throughout training programs and tie recognition directly to milestone achievement. For example, recognize trainees when they:
- Complete onboarding and initial security training
- Earn their first professional certification
- Successfully handle their first incident response independently
- Complete specialized technical training in focus areas
- Achieve specific tenure milestones (3 months, 6 months, 1 year)
- Transition from trainee to full security analyst or specialist roles
Competency Framework Alignment: Many security organizations use competency frameworks defining expected knowledge and skills at different career levels. Link recognition to demonstrating competencies appropriate for trainee progression. This creates transparency about development expectations while providing concrete recognition triggers.
Certification and Education Support: Recognize certification achievements prominently. Organizations investing in trainee certification programs should celebrate successful completion, demonstrating that educational investment is valued and that continuing education is expected and supported.
Balancing Individual and Team Recognition
Security work requires both individual technical excellence and effective teamwork. Recognition programs should acknowledge both dimensions:
Individual Achievements: Celebrate personal milestones, certifications, technical accomplishments, and professional growth. Individual recognition validates personal effort and demonstrates that the organization notices each trainee’s development.
Team Contributions: Recognize trainees’ participation in team projects, collaborative incident response, knowledge sharing, and support for colleagues. Team recognition reinforces that security effectiveness depends on collective capability, not just individual heroics.
Mentor Recognition: Acknowledge experienced security professionals who invest time mentoring trainees. This creates positive reinforcement for mentorship while demonstrating organizational commitment to development culture.

For organizations implementing employee recognition touchscreen displays, consider featuring both individual trainee profiles and team achievement content that highlights collaborative security work and collective accomplishments.
Timing and Frequency Considerations
Recognition timing significantly impacts effectiveness:
Immediate Recognition: Some achievements warrant immediate acknowledgment—successful first incident response, identifying significant security issues, or handling challenging situations effectively. Immediate recognition, even informal acknowledgment from managers or mentors, reinforces desired behaviors while the achievement remains fresh.
Milestone Recognition: Formal recognition tied to defined milestones (certifications, program completion, tenure) can be planned and celebrated more substantially. These become anticipated events that trainees work toward.
Continuous Recognition Culture: Beyond formal programs, cultivate ongoing informal recognition where team members regularly acknowledge colleagues’ contributions, managers provide positive feedback proactively, and learning moments are celebrated rather than punished.
Periodic Celebration Events: Consider quarterly or semi-annual events celebrating trainee cohort achievements, providing opportunities for trainees to present their work, share learning experiences, and receive recognition in front of leadership and colleagues.
Technology Platform Selection
Organizations implementing digital recognition for security trainees should evaluate platforms offering:
Security-Appropriate Content Management: Ensure recognition platforms don’t expose sensitive information about security operations, tools, or procedures. Recognition content should celebrate trainee achievements without revealing security details that could inform adversaries.
Integration Capabilities: Consider whether recognition platforms can integrate with learning management systems tracking training completion, human resources systems maintaining certification records, or security information systems documenting trainee contributions to security operations.
Accessibility and Visibility: Recognition displays should be accessible to all security team members, not just trainees. Consider both physical displays in security operations centers and digital platforms accessible remotely for distributed security teams.
Content Flexibility: Platforms should accommodate diverse content types including written profiles, photographs, video testimonials, certification documentation, project descriptions, and timeline visualizations showing trainee progression.
Privacy Controls: Security trainees may have different comfort levels regarding public recognition. Platforms should allow trainees to review and approve content before publication and provide options to limit certain personal information while still celebrating professional accomplishments.

Organizations exploring touchscreen software solutions for recognition displays should prioritize platforms designed for professional environments with appropriate security controls and content management capabilities.
Best Practices for Security Trainee Recognition
Creating Psychologically Safe Recognition
Cybersecurity involves learning from failures, analyzing mistakes, and acknowledging vulnerabilities. Recognition programs must balance celebrating achievements with maintaining psychological safety for learning:
Normalize Learning Process: Recognition content should acknowledge that all security professionals—including those now senior—were once trainees who made mistakes and learned through experience. Feature narratives describing how recognized professionals overcame challenges rather than implying expertise came easily.
Celebrate Growth Over Perfection: Recognize progress, improvement, and development rather than only perfect performance. A trainee who struggled with network security concepts initially but demonstrated significant improvement through effort deserves recognition for that growth trajectory.
Private vs. Public Recognition: Some achievements merit public celebration; others might embarrass trainees or expose mistakes unnecessarily. Calibrate recognition visibility appropriately. Major certifications and clear successes work well for public recognition; recovery from difficult learning experiences might be better acknowledged privately.
Avoid Competitive Dynamics: Security teams benefit from collaboration, not internal competition. Design recognition programs that celebrate many trainees’ achievements rather than creating perceptions that only top performers receive acknowledgment. Multiple recognition categories ensure diverse contributions are valued.
Ensuring Equitable Recognition
Diverse Contribution Acknowledgment: Different security specializations require different skills. Recognize contributions across technical analysis, incident response, security engineering, compliance work, and security awareness equally, avoiding bias toward particular security domains.
Career Path Diversity: Security careers follow many paths—some emphasize technical depth, others leadership, still others breadth across security domains. Recognition should celebrate progression along different career trajectories without privileging one path over others.
Representation Monitoring: Track who receives recognition over time, ensuring that women, underrepresented minorities, and professionals from diverse backgrounds receive equitable acknowledgment. Unconscious bias can affect recognition patterns; explicit monitoring helps identify and correct disparities.
Accessibility: Ensure recognition ceremonies, displays, and programs are accessible to all security team members regardless of disability, remote work status, or schedule constraints. Consider recording recognition events for asynchronous viewing and providing digital access to recognition content for distributed teams.
Connecting Recognition to Career Development
Development Planning Integration: Use recognition milestones as inputs to development planning conversations. When trainees achieve significant milestones, schedule discussions about next development steps, career goals, and opportunities for increasing responsibility.
Visibility to Leadership: Ensure security leadership regularly reviews trainee recognition, demonstrating attention to talent development and providing opportunities for leadership to engage personally with high-performing trainees.
Promotion Criteria Alignment: Recognition achievements should align with criteria for promotion from trainee to analyst or specialist roles. When trainees understand that recognized accomplishments demonstrate readiness for advancement, recognition motivates progression along defined career paths.
Professional Portfolio Building: Help trainees document recognized achievements as part of professional portfolios useful for future career opportunities, whether internal advancement or external market positioning. Recognition serves both immediate motivational purposes and longer-term professional development.

Organizations implementing comprehensive digital recognition solutions should ensure recognition systems support career development conversations and provide documentation useful for promotion decisions and professional portfolio development.
Measuring Recognition Program Effectiveness
Quantitative Metrics
Retention Metrics: Track trainee retention rates before and after recognition program implementation. Calculate retention at key intervals (6 months, 1 year, 2 years post-hire) and compare against baseline periods or industry benchmarks.
Time to Competency: Measure how quickly trainees achieve defined competency milestones or complete certification programs. Effective recognition programs that motivate learning should show improvements in time-to-competency metrics.
Certification Achievement Rates: Track what percentage of trainees successfully complete targeted certification programs and compare against baseline periods. Recognition tied to certification completion should increase achievement rates.
Internal Mobility: Monitor how many trainees successfully promote to analyst or specialist roles within the organization versus leaving for external opportunities. Effective recognition supporting career development should improve internal advancement rates.
Engagement Metrics: If using digital recognition platforms, track interaction data including profile views, video completions, search queries, and session durations indicating level of engagement with recognition content.
Qualitative Feedback
Trainee Satisfaction Surveys: Regularly survey security trainees about their experience with recognition programs, asking whether they feel valued, whether recognition aligns with their actual contributions, and what improvements would make recognition more meaningful.
Manager Perspectives: Gather feedback from security managers about recognition program impact on trainee motivation, team dynamics, and retention outcomes based on their direct observation.
Mentor Input: Survey experienced security professionals mentoring trainees about whether recognition programs support their mentorship efforts and influence trainee development positively.
Exit Interview Analysis: When trainees do leave, analyze exit interview data for patterns related to recognition, acknowledgment, and perceived value. Understanding why recognition wasn’t sufficient to retain departing trainees provides improvement insights.
Continuous Improvement
Recognition programs should evolve based on feedback and metrics:
Regular Review Cycles: Schedule quarterly or semi-annual recognition program reviews examining quantitative metrics, qualitative feedback, and implementation challenges to identify improvement opportunities.
Pilot Testing Changes: When considering program modifications, pilot test changes with smaller trainee cohorts before organization-wide rollout, gathering feedback to refine approaches.
Benchmarking: When possible, benchmark recognition practices against other security organizations or broader industry standards to identify innovative approaches worth considering.
Industry-Specific Applications
Corporate Security Operations Centers
Large enterprise security operations centers often employ multiple trainees simultaneously, creating opportunities for cohort-based recognition programs. SOC environments benefit from recognition that:
- Celebrates first solo shift completions and independent incident triage
- Acknowledges contribution to incident response team efforts
- Recognizes threat detection and alert quality improvements
- Highlights effective communication with stakeholders during incidents
- Celebrates completion of SOC analyst training certifications
Managed Security Service Providers
MSSPs operating client security services face particular retention challenges as trainees gain experience attractive to client organizations. Recognition programs that emphasize career development paths within MSSP environments, celebrate breadth of experience across diverse client environments, and acknowledge expertise in MSSP-specific tools and procedures can improve retention despite competitive client recruiting.
Financial Services Security Teams
Financial sector security teams operate under intense regulatory requirements and threat landscapes. Trainee recognition should acknowledge:
- Understanding and adherence to financial sector security regulations
- Contributions to compliance and audit requirements
- Handling sensitive financial data with appropriate confidentiality
- Participation in tabletop exercises and security drills
- Specialized training in financial sector threat intelligence
For organizations in highly regulated industries, digital recognition displays provide platforms that can be updated to reflect changing compliance requirements and regulatory training milestones while celebrating security professional development.
Healthcare Security Programs
Healthcare organizations face unique security challenges protecting patient data while supporting clinical operations. Trainee recognition should celebrate:
- Understanding HIPAA requirements and healthcare security contexts
- Supporting security for clinical systems and medical devices
- Balancing security requirements with patient care priorities
- Participating in healthcare security exercises and scenarios
- Specialized healthcare security certifications
Technology Company Security Teams
Technology companies often employ large security organizations with specialized teams. Recognition programs can acknowledge:
- Contributions to product security and secure development practices
- Participation in bug bounty program administration
- Security research and vulnerability discovery
- Open-source security tool contributions
- Conference presentations and external community participation
Organizations seeking to implement recognition programs should consider how interactive touchscreen displays can be customized to reflect industry-specific security contexts and specialized recognition categories relevant to their particular security operations.
Overcoming Implementation Challenges
Budget Constraints
Organizations may question whether recognition program investment is justified given competing security priorities. Address this through:
ROI Documentation: Calculate turnover costs for security trainees and project retention improvements from recognition programs. Even modest retention improvements typically justify recognition program costs through reduced recruitment, onboarding, and lost productivity expenses.
Phased Implementation: Begin with lower-cost recognition approaches like structured peer recognition, manager acknowledgment programs, and small celebration events before investing in technology platforms or elaborate recognition systems. Demonstrate value at smaller scale before expanding investment.
Shared Infrastructure: If organizations already operate recognition programs for other employee populations, leverage existing platforms and infrastructure for security trainee recognition rather than creating entirely separate systems.
Time Investment Concerns
Security managers may resist recognition programs requiring significant time investment given operational demands. Address concerns through:
Process Integration: Build recognition into existing processes rather than creating separate activities. For example, integrate recognition into regular one-on-one meetings, team meetings, and performance review cycles rather than scheduling additional dedicated recognition time.
Peer Recognition Systems: Enable peer-to-peer recognition where team members acknowledge colleagues’ contributions, distributing recognition responsibility across teams rather than concentrating it solely with managers.
Recognition Champions: Designate specific team members passionate about professional development and recognition to coordinate programs, reducing burden on busy security managers while maintaining program momentum.
Measuring Soft Skills and Culture
While technical achievements like certifications are easily documented, recognizing softer contributions like teamwork, mentorship, or cultural contributions presents challenges. Address this through:
Behavioral Indicators: Define specific observable behaviors indicating desired soft skills. Rather than vaguely recognizing “teamwork,” recognize specific actions like “proactively shared threat intelligence findings with application security team” or “volunteered to help new trainee learn SIEM platform.”
Multi-Source Feedback: Gather input from multiple sources including peers, managers, mentors, and stakeholders outside security teams to assess softer contributions more comprehensively than manager observation alone allows.
Narrative Recognition: Use storytelling to illustrate soft skill contributions through specific examples rather than abstract statements. Describe situations where trainees demonstrated resilience, collaboration, or ethical behavior through their actions in particular contexts.
Building Long-Term Recognition Culture
Sustainable recognition extends beyond formal programs to organizational culture where acknowledgment becomes natural and routine.
Leadership Modeling
Security leadership must actively participate in recognition for it to become embedded in organizational culture. When chief information security officers, security directors, and security managers regularly acknowledge trainee contributions publicly, it signals that recognition matters and sets expectations for behavior throughout security organizations.
Peer Recognition Encouragement
Create opportunities and expectations for peer-to-peer recognition. Security professionals who receive meaningful acknowledgment from colleagues they respect often value peer recognition as highly as formal management recognition. Encourage regular team recognition moments, peer nomination of colleagues for formal recognition programs, and structured mechanisms for colleagues to express appreciation.
Integration with Performance Management
Connect recognition to performance management processes without making recognition feel transactional. Recognition achievements should inform performance evaluations and development planning while maintaining the authentic appreciation that makes recognition meaningful.
Storytelling and Legacy
Use recognition as opportunity for storytelling that transmits organizational values and security culture. When celebrating trainees who embody desired characteristics, describe specifically what they did and why it matters. These stories become cultural artifacts illustrating what the organization values and expects.
Organizations implementing digital recognition platforms gain powerful storytelling capabilities through multimedia content that brings trainee achievements to life more vividly than text alone allows.
Conclusion: Investing in Security’s Future Through Recognition
The cybersecurity profession faces unprecedented challenges: persistent adversaries, expanding attack surfaces, evolving technologies, and chronic talent shortages. In this demanding environment, developing the next generation of security professionals represents one of the most important investments organizations can make. Yet development requires more than technical training—it requires creating environments where trainees feel valued, see clear development paths, receive acknowledgment for their efforts, and commit to organizations invested in their success.
Strategic recognition programs specifically designed for cybersecurity trainees provide powerful tools for retention, motivation, and culture building. When implemented thoughtfully, these programs accelerate trainee development, reduce attrition, strengthen team cohesion, and ultimately improve organizational security by cultivating stable, skilled, committed security teams.
Key Success Factors for Cybersecurity Trainee Recognition:
- Design recognition around security-specific competencies and development milestones
- Balance individual achievement acknowledgment with team contribution recognition
- Create psychologically safe recognition that normalizes learning processes
- Ensure equitable recognition across diverse security specializations and career paths
- Integrate recognition with career development planning and advancement criteria
- Measure program effectiveness through retention, competency, and satisfaction metrics
- Build sustainable recognition cultures beyond formal programs
The investment in recognition programs represents investment in security capability, organizational resilience, and professional development. Organizations that recognize their security trainees meaningfully will find themselves better positioned to attract talent, develop capabilities, and retain the skilled professionals necessary for defending against sophisticated threats.
Ready to transform how your organization develops and retains cybersecurity talent? Solutions like Rocket Alumni Solutions provide platforms specifically designed for professional recognition, offering intuitive content management, multimedia capabilities, and interactive features that make celebrating security trainees both meaningful and sustainable. Your organization’s security depends on the professionals you develop—ensure they know their contributions are valued, their progress is recognized, and their future is bright.